Encryption: how it works, why we should care, and what we can do
The first part of Marc Richly's three-part series on encryption
Over 2000 years ago, the Roman dictator Julius Caesar developed a method to ensure that only the recipient of a message receives it. Often enough others were a little too interested what the dictator had on his mind, so the Caesar cipher was born (ABCDE… becomes e.g., CDEFG…). It has since fallen out of favour due to the ease with which it can be cracked, but was used as recently as 1915 by the Russian army, whose soldiers struggled to use more advanced ciphers. Nonetheless, the Caesar cipher is still a particularly famous example of an encryption technique.
Today, encryption is more relevant than ever – most of us use it daily without ever realising it. This article is the first in a three-part series examining its uses in digital communication. It will show how encryption in digital communication works. The second article will address why we should care about encryption, and the last one will provide a how-to guide on securing your digital life.
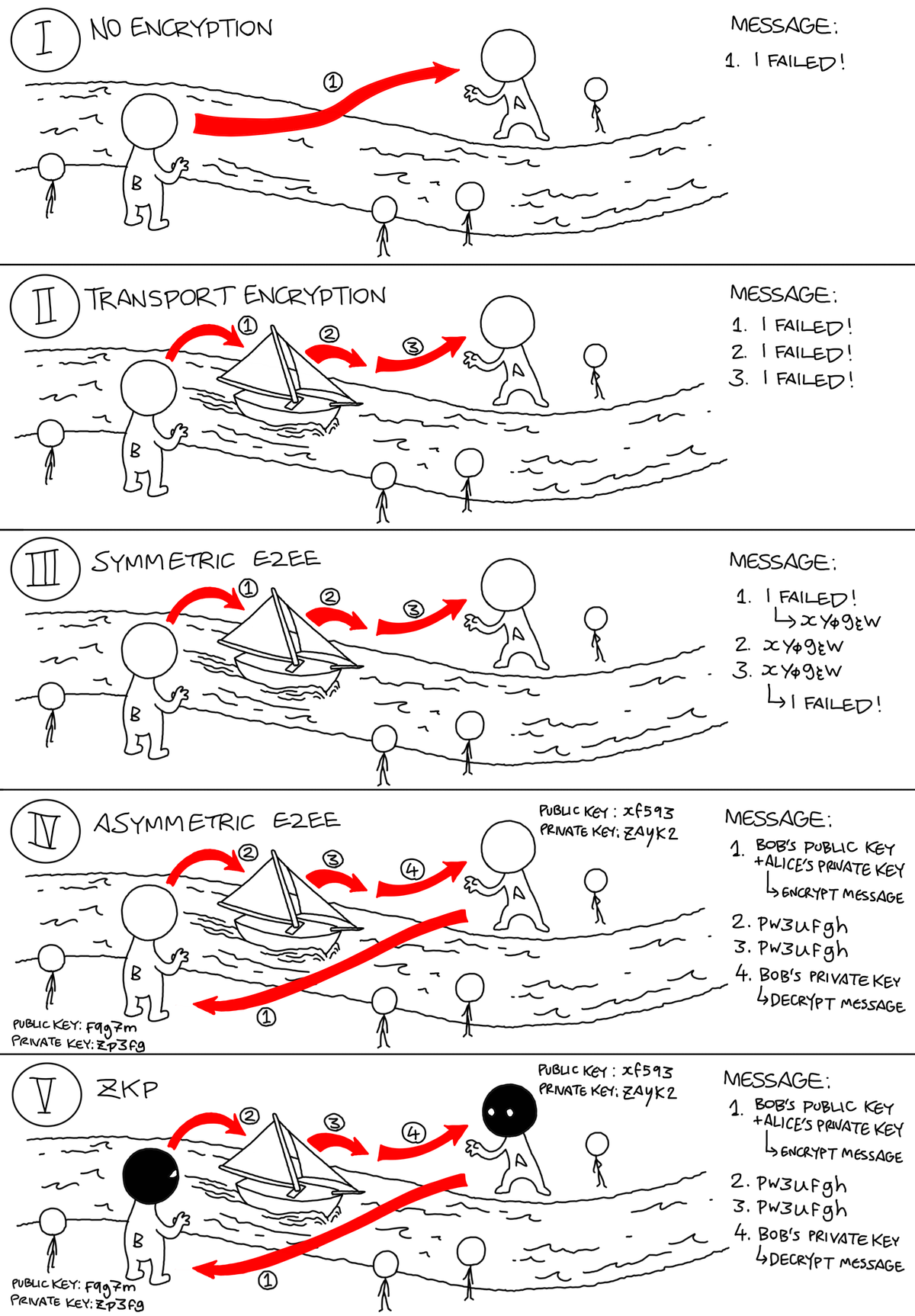
To understand different encryption types, imagine standing with many other strangers at a river. You want to tell your friend who is standing on the on the other side of the river something confidential – you have failed your last exam. In all scenarios we must look at two things: Who can access the information (let us call this content data), and who can see that a communication takes place (let us call that meta data).
Meta data is very valuable for analytics operations in companies. It can be used to identify close contacts and offer personalised advertisements (your friend bought a MacBook so you may also be interested). Governments and security agencies can use meta data to identify contacts of criminals and other persons of interest.
1) No encryption
Your first option is to simply shout the message across the river. Other people can see that you have communicated with your friend (meta data) and can easily understand what you say (content data).
2) Transport encryption
Second scenario: You whisper to a fisherman on your side of the river that you failed the last exam. He rows to the other side of the river, and passes the message to your friend by whispering in his ear. This is already more secure, but two problems arise: You must trust the fisherman that he is not telling anyone else (he has access to the content data), and other people still see that you have transferred a message (meta data). This is most commonly used to encrypt emails.
3) Symmetric encryption and End-to-End encryption (E2EE)
Third scenario: as you and your friend are both nerds, you have developed a unique language. You either shout over the river or use the fisherman – in both ways only people who know the language can understand you. This means your message itself is secured (content data). People still see that you send a message to your friend on the other river side (meta data), but you do not have to trust the fisherman anymore. This form of encryption is called symmetric encryption, where both sides use the same key (here the secret language) to transfer information. The new risk is now that someone cracks the code and can understand the message, so let us look at the next level of encryption.
4) Asymmetric encryption and End-to-End encryption (E2EE)
Fourth scenario, you both have created two mathematical keys, one public, one private key. Everyone shares their public key openly, while keeping their private key to themselves. When you have the public key of your friend, you can encrypt a message, shout it over (or send it with the fisherman), and only your friend can open the message with their private key. Your friend’s public key and private key are mathematical connected, but it is virtually impossible to guess the private key from knowing the public key.
Asymmetric encryption is a standard in encryption, symmetric encryption is not considered secure anymore. Asymmetric encryption is used by WhatsApp, https websites, and bitcoin.
5) Zero-Knowledge Principle (ZKP)
Fifth scenario, you do as in scenario four, but this time you and your friend wear masks so nobody knows who you are. In this way, the information (content data) is secure, and one can see that a message gets transferred from the one river side to the other one, but it is impossible to tell who communicates with who (meta data). This form of digital communication encryption is considered a gold standard. The most prominent communication service that offers ZKP in addition to E2EE is Signal (messaging app like WhatsApp).








